How is SOC 2 Important in Multifamily IoT?
With an increasing number of multifamily IoT providers, prospective customers have every right to know and ask about an organization’s security practices. These companies’ technologies touch sensitive user information surrounding the daily lives of residents, property managers, and more, and must be as secure as possible.
To start, an easy way to gauge an organization’s level of security is to ask for a SOC 2 (Service Organizations Controls, pronounced as “sock two”) report. There are several areas of security to discuss outside of this assessment but for now, let’s dive into SOC 2.
What is SOC 2?

The American Institute of Certified Public Accountants developed the (AICPA) SOC 2 as an auditing procedure to ensure that companies protect their clients’ information. Licensed CPAs, not affiliated with the company requesting the audit, carry out the process so that they can be unbiased. The auditors lead various activities to test a company’s security controls like reviewing current security policies, talking with relevant employees, and visiting the on-site facilities, like the office and/or data centers.
There are two types of SOC 2 reports: Type I and Type II. Both test for the effectiveness of an organization’s controls. The main difference is that SOC 2 Type I looks at the organization’s security and privacy controls at one point in time, while SOC 2 Type II reports on the organization’s cybersecurity effectiveness over a longer period of time, usually six months to a year.
The rigorous auditing process takes several months to complete and measures a company’s security preparedness. The qualifications required with a SOC 2 Type II attestation are not a simple list of items to check off, or requirements that a company could accidentally stumble upon.
A SOC 2 report offers detailed evidence that a company is trustworthy and is actively putting in a lot of effort to be cyber secure.
What does each area of the Trust Services Criteria cover?
The five areas that SOC 2 focuses on, also known as Trust Services Criteria, are Privacy, Security, Availability, Processing Integrity, and Confidentiality .
- Privacy: protection for personal information, and this is often a priority if the organizations handles health information
- Security: protection against any sort of unauthorized action
- Availability: the system is available to customers as established in contracts
- Processing integrity: system processing is timely and accurate, and this is often a priority if the organization handles financial transactions
- Confidentiality: protection for confidential information
A security-driven company would want the conversation to continue past, “Do you have a SOC 2 report?” Organizations with security measures in order will typically and readily offer SOC 2 documentation, which includes a security overview walkthrough, penetration testing results (with redacted exact vulnerabilities), and static code review results.
A prospective customer has the responsibility to ask for and learn about these security considerations to be as informed as possible on their solutions providers’ priorities.
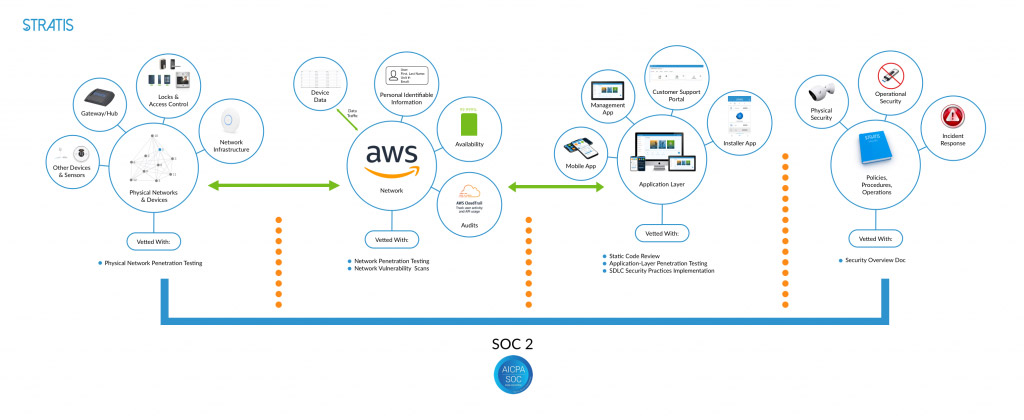
STRATIS is proud to have received its SOC 2 compliance after almost half a year of extensive examination. The above image shows the different areas of the company that the audit team reviewed, like they vetted physical networks and devices with physical network penetration testing, the network with network penetration testing an network vulnerability scans, the application layer with static code review, application-layer penetration testing, and SDLC security practices implementation, and policies, procedures, and operations with security overview document.
As mentioned above, a security-driven organization would want the conversation to continue past, “Do you have a SOC 2 report?” Organizations that have security measures in order will typically (and readily) offer to provide SOC 2 documentation, a security overview walkthrough, penetration testing results (with redacted exact vulnerabilities), and static code review results.
Want to learn more about SOC 2? Check out this article that explains the differences between SOC 2 and ISO, another security auditing process.
STRATIS®, a RealPage Company, creates smart apartments and intelligent buildings and is the only platform of its kind built for the complexities of multifamily and student housing. STRATIS is installed worldwide across the U.S., in Japan, the UK, EU, and Latin America. STRATIS now serves hospitality, retail, and small to mid-size commercial, as well. STRATIS is an Inc. Magazine “Fastest Growing Company in America” and a Top Ten Entrepreneur Magazine “Best Company in America.” STRATIS was recently acquired by RealPage to enable STRATIS Smart Building, a more connected lifestyle, and unleash hidden yield through new revenue streams.
STRATIS®, a RealPage Company, creates smart apartments and intelligent buildings and is the only platform of its kind built for the complexities of multifamily and student housing. STRATIS is installed worldwide across the U.S., in Japan, the UK, EU, and Latin America. STRATIS now serves hospitality, retail, and small to mid-size commercial, as well. STRATIS is an Inc. Magazine “Fastest Growing Company in America” and a Top Ten Entrepreneur Magazine “Best Company in America.” STRATIS was recently acquired by RealPage to enable STRATIS Smart Building, a more connected lifestyle, and unleash hidden yield through new revenue streams.